The Real Risk After the Coinbase Hack Isn’t Just the Breach - It’s What Happens Next
Beyond the 2025 Coinbase phishing attack: How fraudsters will leverage the leaked data to create detailed segmentation for far more convincing impersonations.

In May, Coinbase confirmed a serious data breach involving bribed third-party support agents, exposing sensitive customer information that is now fueling a wave of advanced phishing and social engineering attacks. The incident, revealed in an SEC filing, could cost the company up to $400 million to fix.
The attackers obtained access to internal support tools and stole customer data including names, emails, addresses, phone numbers, partial Social Security numbers, masked bank details, and government ID images.
While passwords and private keys were not compromised, the breach has significantly increased the risk of business email compromise (BEC), impersonation, and a growing number of sophisticated attack strategies employed by threat actors to defraud users.
Now that scammers have access to sensitive customer data, they can identify and target high-value individuals with precision. In this breakdown, we unpack the most common social engineering tactics used in crypto phishing scams, and what security leaders can do to protect their users, reputations, and revenue.
What Comes After the Coinbase Data Breach? Predicting the Next Wave of Phishing Attacks
From Nets to Spears - How Leaked Data Enables Segmented Targeting and Spear-phishing
When scammers gain access to personally identifiable information (PII) - like names, email addresses, phone numbers, and wallet history, they can build segmented hitlists based on factors like:
- Demographics (age, job title, geography)
- Behavioral patterns (transaction volume, trading frequency, known associations)
- Risk profiles (e.g. users who frequently move large amounts of crypto, or have ties to high-value institutions)
With enough leaked data, attackers can create a playbook of deception - tailoring each scam to the target’s digital behavior and demographic footprint, making their social engineering not just plausible, but alarmingly personal.
1. Support Staff Impersonating
In several examples shared on X, scammers sent emails posing as Coinbase Support, urging users to switch to self-custodial wallets. The messages included instructions for downloading the official Coinbase Wallet, with an April 1 deadline to pressure recipients into acting quickly.
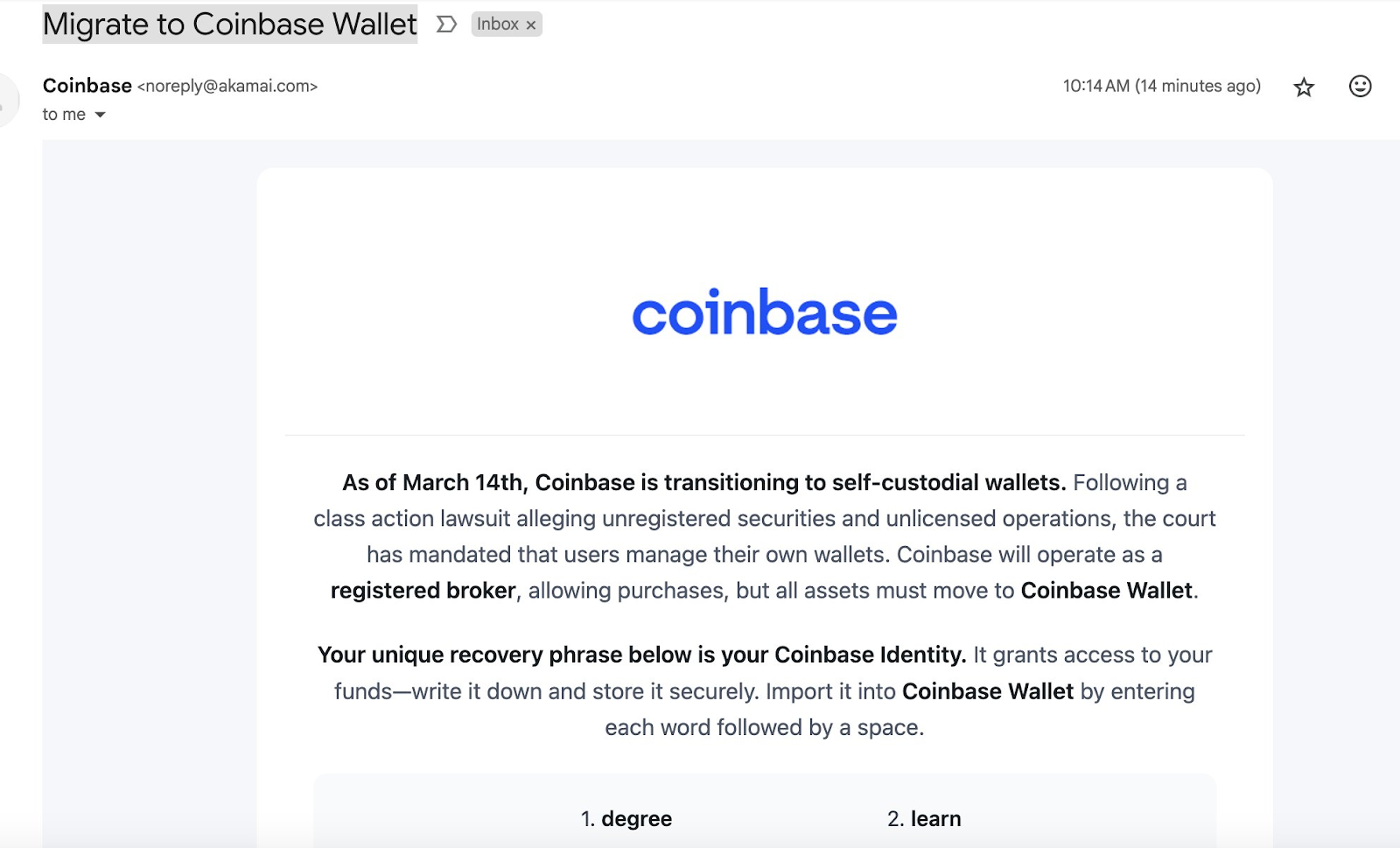
Scammers posing as support staff send deceptive emails urging users to download the app and create new wallets using recovery phrases they've provided. These phrases are controlled by the attackers, and as soon as the wallet is set up, any funds transferred in can be immediately stolen.
Another similar tactic involves phone impersonation. Scammers contacting victims pretending to be Coinbase support will cite a suspicious login attempt and walk the target through a fake password reset, stealing the victim’s login credentials along the way.
Specific Tactics Attackers Use with Leaked Data: Personalized Support Impersonation
With access to user-specific data, such as account balances, recent transaction details, or past support tickets, attackers can lower suspicion and convincingly impersonate customer support agents. For example, a scammer posing as a Coinbase support rep might email a user about a “flagged $5,000 transfer” from their actual wallet address, citing the last four digits of their account. The user, already primed with real data, may be persuaded to “verify” their identity by clicking a malicious link or sharing a 2FA code - unknowingly handing over control of their funds
2. Fake Crypto Projects and Airdrops
Fraudsters impersonate real crypto projects using phishing links distributed through hacked or impersonated social media accounts (e.g. Discord, Twitter/X, etc.) and spoofed websites, offering fake token airdrops.
Airdrops are a common method in crypto for distributing free tokens - typically used to support marketing, grow user bases, or strengthen community engagement. Legitimate airdrops aim to reward early supporters, boost awareness, or drive on-chain activity.
Scammers leverage the trust users place in these brands and community channels to convince them to act quickly. They exploit user greed and curiosity by promising free tokens (fake airdrops) in exchange for sensitive actions such as sharing private keys, signing malicious contracts or paying gas fees.
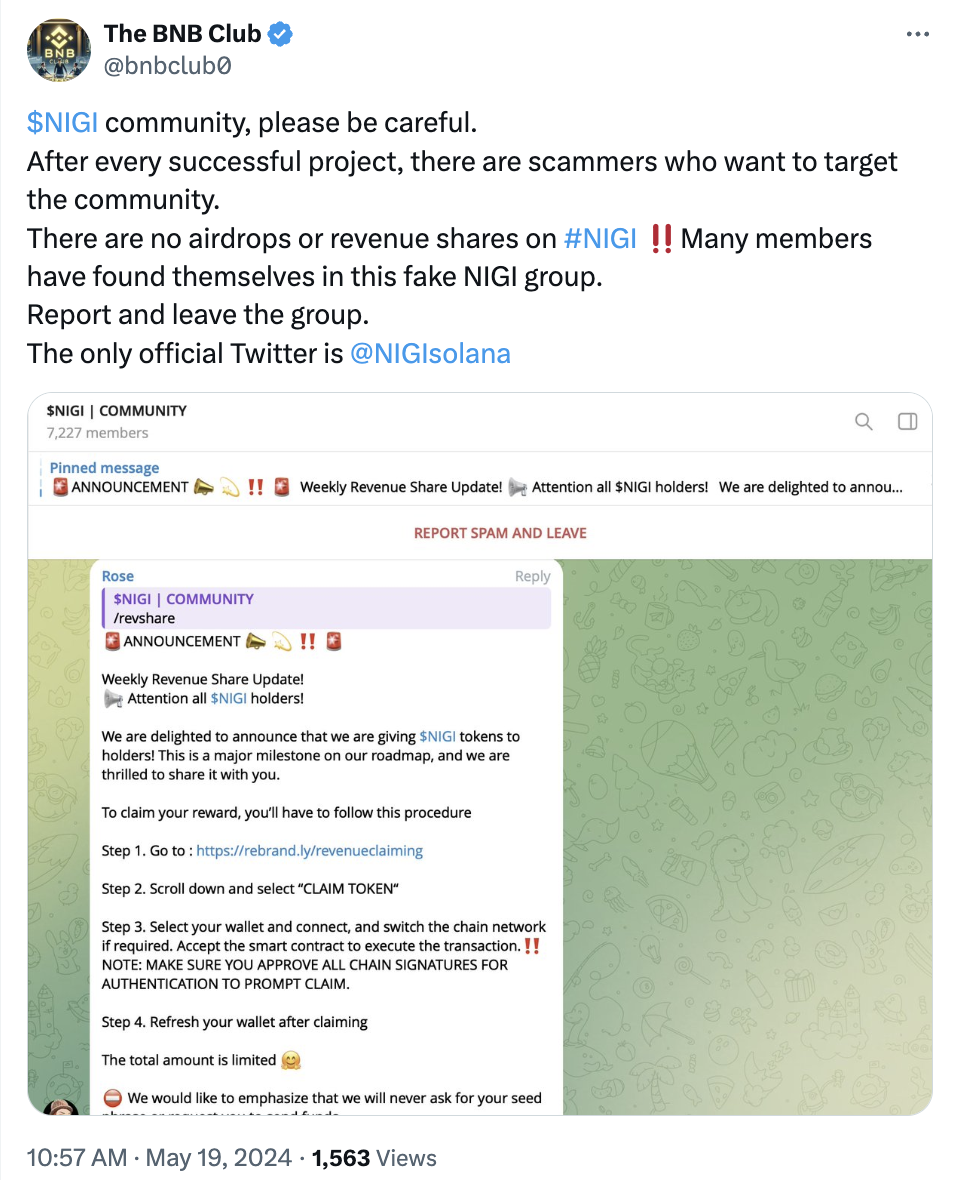
Specific Tactics Attackers Use with Leaked Data: Custom-Built Fake Communities
Scammers can create online groups, Discord servers, or Telegram channels that mirror legitimate crypto or Web3 communities a target is likely to engage with. For example, a victim who frequently interacts with Solana-based NFT communities might be invited to a Discord channel promoting a “founders-only mint” - complete with fake endorsements and countdowns, ultimately leading them to sign a malicious contract that drains their wallet.
3. Google Ads Malware
Threat actors are abusing Google Ads to distribute malware under the guise of legitimate crypto tools like wallet apps or trading software. These malicious ads closely imitate a legitimate domain and can appear at the top of search results, leading unsuspecting users to fake websites that mimic real brands.
Once the malware is installed, it can:
- Monitor for private key inputs: The malware watches keystrokes and browser activity, waiting for users to enter private keys or seed phrases into web forms or apps.
- Hijack clipboard transactions: When users copy a wallet address to send funds, the malware detects the copied string and replaces it with the attacker’s address, redirecting transactions in real time.
- Search local files for seed phrases: The malware combs through browser data, plaintext files, and wallet backups on the user’s device, looking for sensitive recovery phrases or configuration files that could grant access to funds.
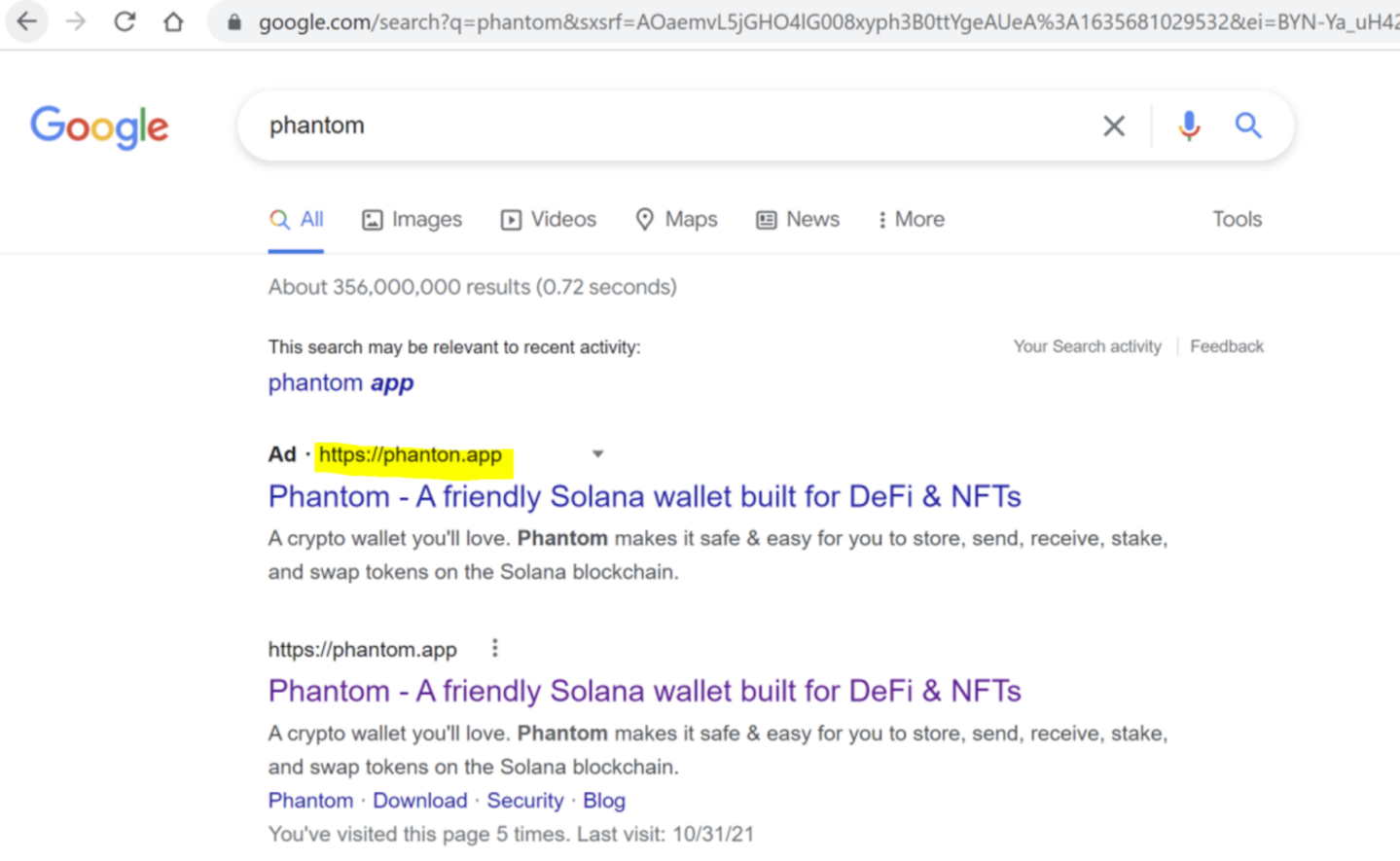
Specific Tactics Attackers Use with Leaked Data: Targeted Ads and Lures
With detailed demographic and behavioral data, attackers can craft phishing ads that resonate with specific interests, professions, or geographies. For example, a scam targeting DeFi investors might promote a fake staking opportunity, while another aimed at Web3 developers might promise early access to a new protocol. The more tailored the bait, the higher the click-through and conversion rate for the scam.
4. Fake Job Postings and Employment Scams
On June 6, the FBI reported a surge in scam ads promoting fake work-from-home jobs. Scammers will impersonate recruiters at recognizable companies in tech and crypto to build credibility, then share links to fake “pre-employment tests” or downloads that are used to install malware and gain access to sensitive information on the victim’s device.
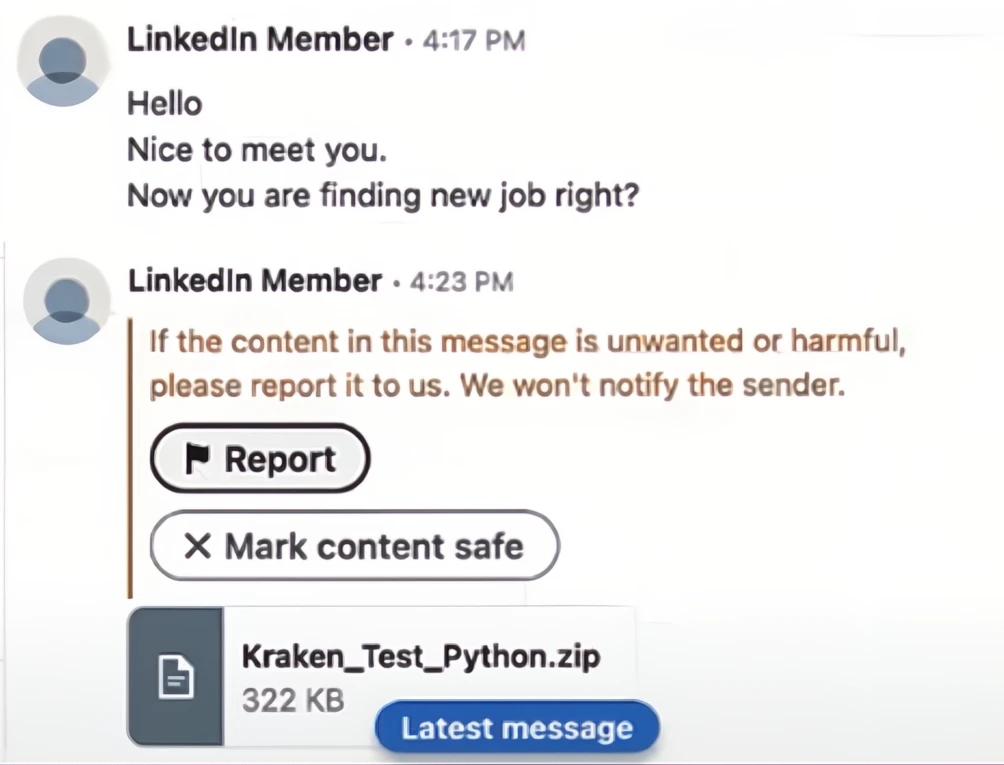
“The actors usually attempt to initiate prolonged conversations with prospective victims to build rapport and deliver malware in situations that may appear natural and non-alerting. The actors usually communicate with victims in fluent or nearly fluent English and are well versed in the technical aspects of the cryptocurrency field.” - FBI.
Specific Tactics Attackers Use with Leaked Data: Professionally Tailored Fake Job Offers
Knowing someone’s employment background allows attackers to craft fake job postings or outreach messages that align closely with their skills and career path. A designer might receive a job offer from a known design brand, complete with realistic compensation and next steps. The bait often includes malware, credential theft, or social engineering to extract more sensitive info under the pretense of onboarding.
5. Address Poisoning (Wallet Spoofing)
Address poisoning, also called wallet spoofing, exploits a traders’ carelessness and haste during crypto transactions. Scammers create wallet addresses that closely resemble legitimate ones, tricking users into accidentally sending funds to the wrong destination.
Similar to ransomware kits, address poisoning scams are now plug-and-play. Toolkits sold on darknet markets come with intuitive UIs that make it easy for even low-skilled attackers to run sophisticated campaigns. These kits typically include software to generate convincing look-alike wallet addresses, automated scripts to “dust” targets with small transactions, and step-by-step guides for exploiting transaction history to deceive victims.
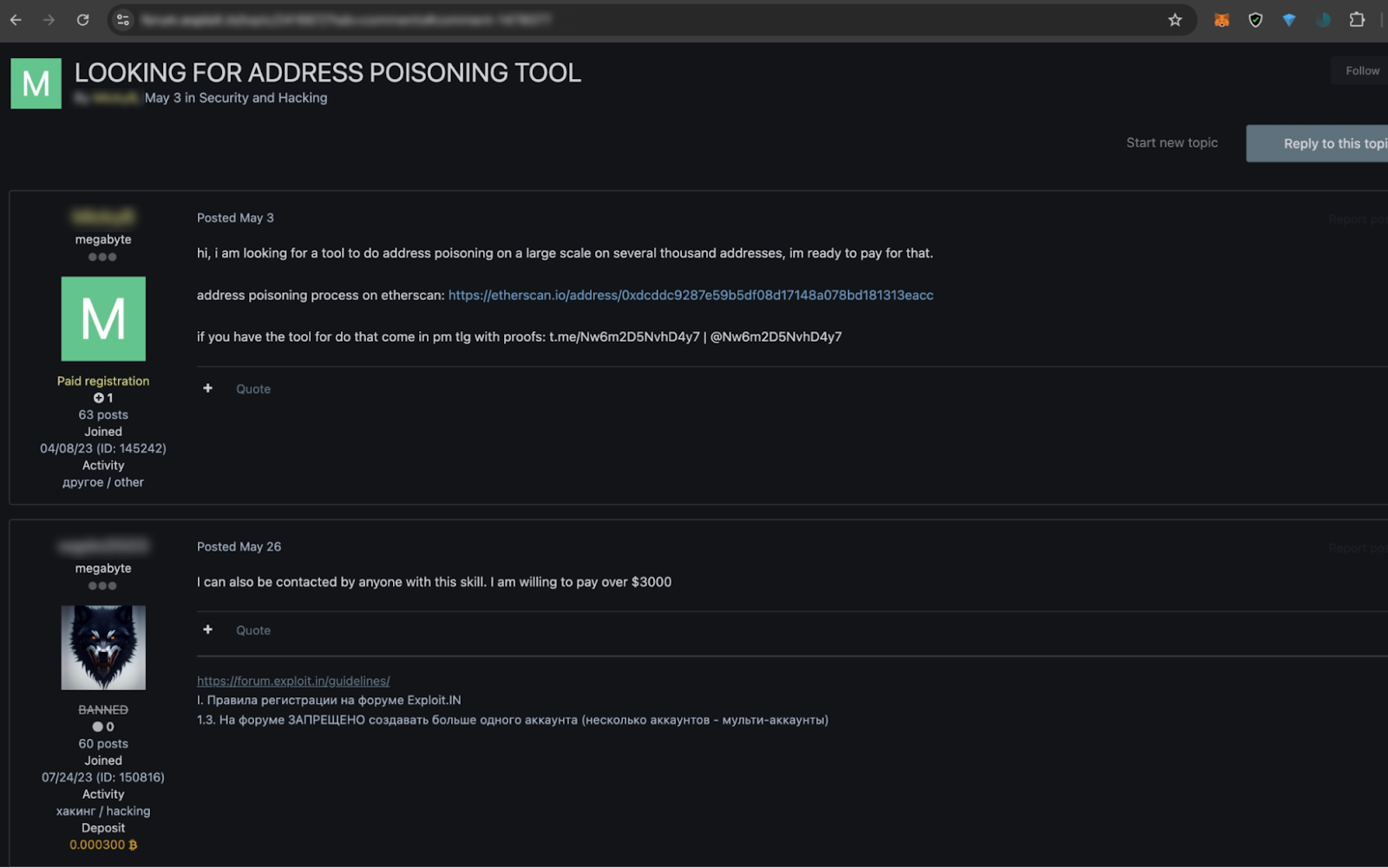
Specific Tactics Attackers Use with Leaked Data: Wallet Spoofing with Familiar Addresses
By analyzing transaction history, scammers can identify wallets a high-value target frequently interacts with. They can then generate addresses that visually resemble those trusted contacts. For example, if a target routinely sends funds to a multisig address ending in “...A3f9,” an attacker might create a near-identical address like “...A3f7” and seed the target’s transaction history with a small transfer. Later, when the user copies the recipient from past activity, they may unknowingly select the spoofed address.
Why These Crypto Scams Work
1. Human error:
Social engineering works because it targets human psychology, not just technical flaws. Scammers exploit fear (e.g., “your account is locked”), urgency (e.g., “download by April 1st), and FOMO (e.g., “limited airdrop offer”) to provoke impulsive action.
Familiarity also plays a role: when messages appear to come from known brands or trusted contacts, users are more likely to engage without scrutiny. Even the most security-conscious people can make mistakes under pressure.
2. Inadequate identity validation on inbound communication
Most digital communication systems, especially email, don’t provide a reliable way to confirm the true identity of the sender. A convincing name, logo, or tone is often enough to fool a recipient into believing a message is genuine.
Email has been a consistent vector of attack for scammers. Without strong sender verification, users have no easy way to distinguish a real message from a fraud. This creates a wide attack surface where impersonation is cheap, scalable, and effective.
3. Traditional tools fall short:
While multi-factor authentication, spam filters, and antivirus software provide important baseline protection, they are often reactive and limited in scope. These tools may catch obvious threats, but they struggle with more sophisticated, multi-layered scams that evolve quickly and mimic normal behavior.
For example, an attacker might build trust over time before making a malicious ask - or compromise someone outside the organization entirely, like a customer or vendor - (in the case of Coinbase). These attacks live in the gray area where traditional defenses fail.
---
Scammers frequently impersonate well-known brands to build trust with their targets. While Coinbase ranked as the most impersonated crypto platform, Meta saw over 25 times as many impersonation attempts.
Phishing and social engineering scams are not confined to the crypto world. Your customers, partners, and brand are increasingly vulnerable to a new wave of scams - supercharged by AI, growing in sophistication, and harder to detect than ever before.
Scammers Target More Than Just Crypto. How Outtake’s Human-Risk Defense Proactively Protects Your Org Against Spear-phishing and Social Engineering Attacks
Good security hygiene is an obvious essential - but it only goes so far. To stop scammers before they ever reach your customers, brands need proactive defense. Outtake is built to identify and neutralize threats before they even land.
- Outtake continuously monitors the public web and digital attack surfaces to detect scam infrastructure, brand impersonation, and emerging phishing campaigns in real time.
- Cut through the digital noise to surface credible threats and act on them fast.
- Our agentic takedown workflows remove malicious domains and fake social accounts before they cause harm.
- We safeguard not just your users - but your customers, vendors, investors, and team
Outtake secures your brand across the entire external threat surface, for every digital identity.

We need a new approach to safeguarding our digital ecosystems.













