Verify what's real. Trust what's Verified.
Outtake Verify is a browser extension that cryptographically verifies your identity and signs your emails.
Cryptographic Certainty
Know who pressed send with mathematical proof, not probabilistic guessing
Stop Account Takeover Damage
Compromised accounts can't send verified emails - attackers lack device-bound authentication
Eliminate Threats at the Source
Report phishing domains directly from email for immediate takedown
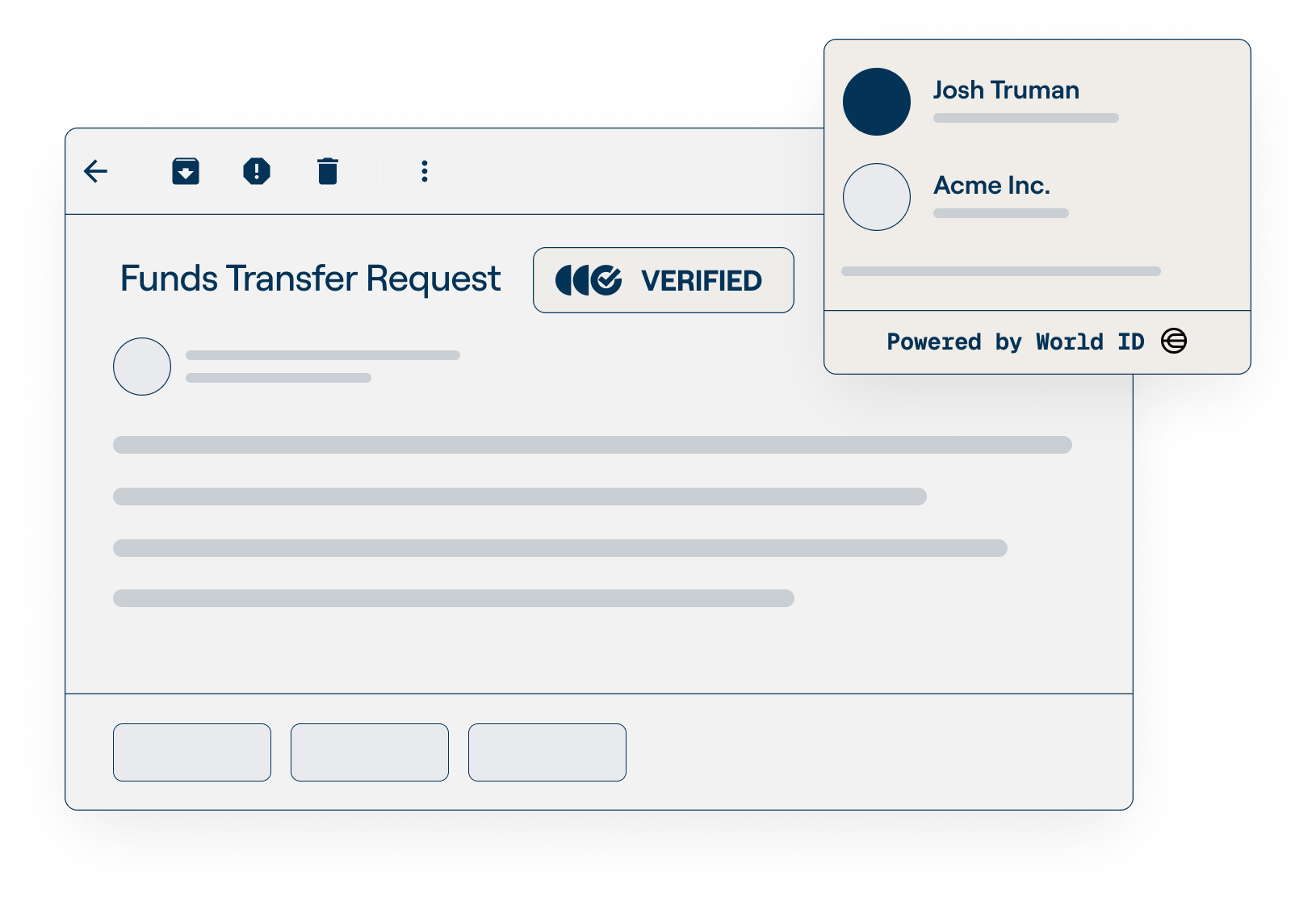
Wire Transfer Requests
Cryptographically verify executive payment approvals, eliminating out-of-band confirmations
Confidential Document Sharing
Ensure sensitive documents come from authenticated sources with message integrity
Partner Communications
Extend trust beyond organizational boundaries by requiring authentication from key vendors
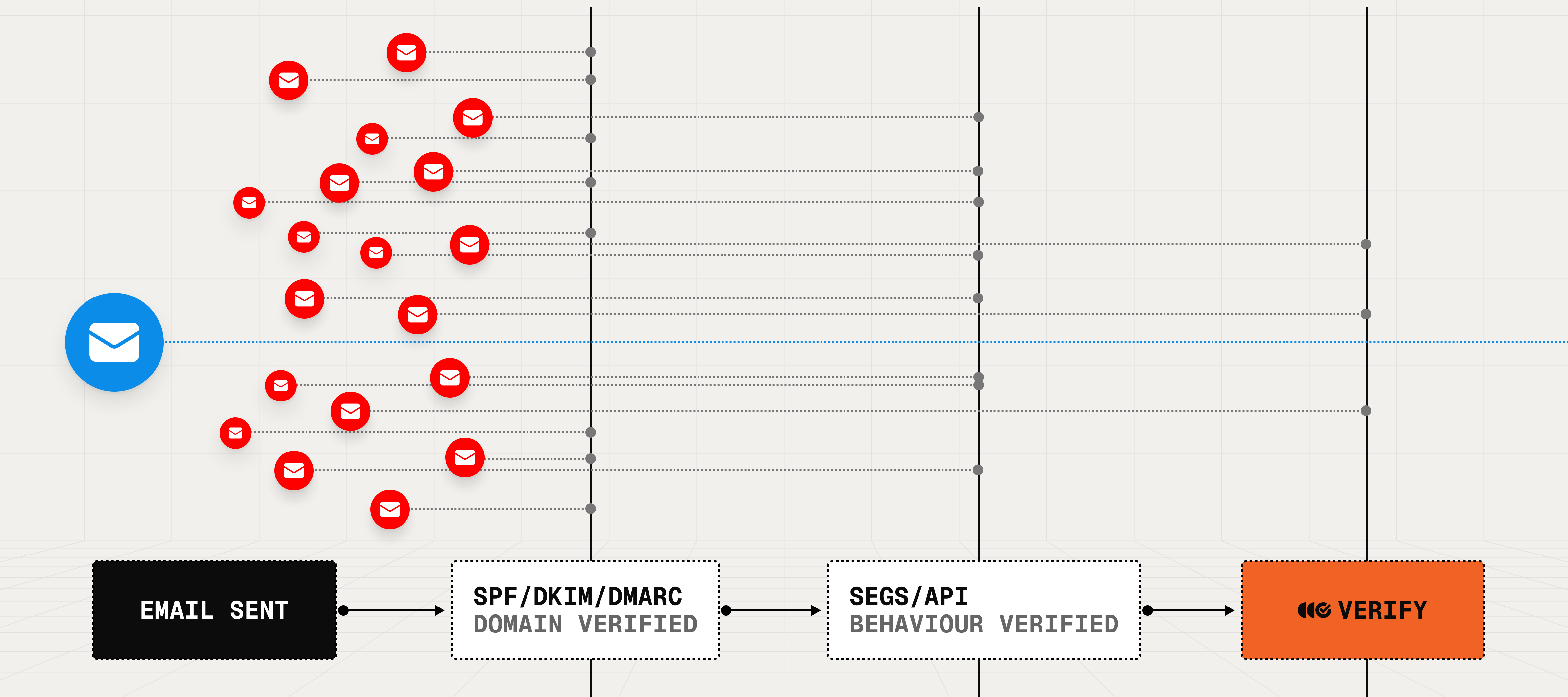
How it works.
Verify complements your existing ML-based filters with deterministic certainty, guaranteeing you’re communicating with trusted counterparties.
1. Secure Onboarding
Integrate with existing SSO and tie employee identities to device-bound passkeys - no certificates required
2. Send Verified
Users hit "Send Verified" and authenticate with their passkey. Email content is hashed and cryptographically signed on-device
3. Receive with Confidence
Recipients see verification badges with full sender details. Filter for verified emails or request verification from counterparts