We're thrilled to announce Outtake Verify for Email: the email security product that guarantees you’re communicating with trusted counterparties.
Designed for enterprise teams and executives that use email for sensitive workflows, Verify is a simple browser extension that cryptographically signs emails with your unique device Passkey or your World ID, ensuring official communication is unmistakable and preventing vendor or executive impersonation or account takeover.
It's free for early partners, easy to deploy, and available now. In this post, we'll explain why email desperately needs this authentication layer, and how Verify delivers it.
Ready to never second-guess an email again?
Situation: Early on at Outtake our team was flooded with phishing emails claiming to be me (Alex). They varied in sophistication and in what they requested from us: personal details, phone numbers, invoices, etc.
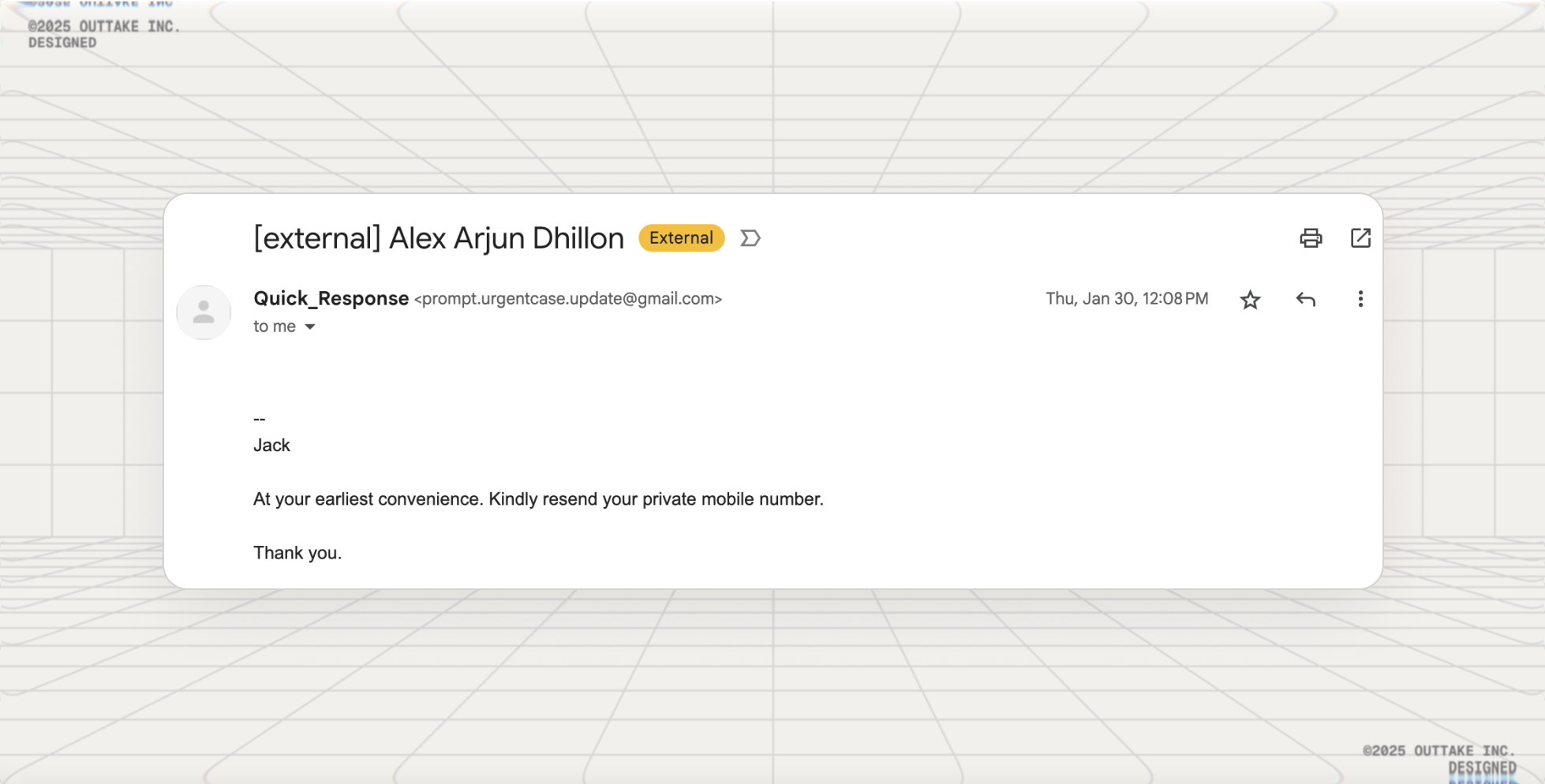
This problem is foundational in email. Email was built in the 1970s for messaging, not security. Anyone can spoof a domain, hijack an account, or craft convincing fakes.
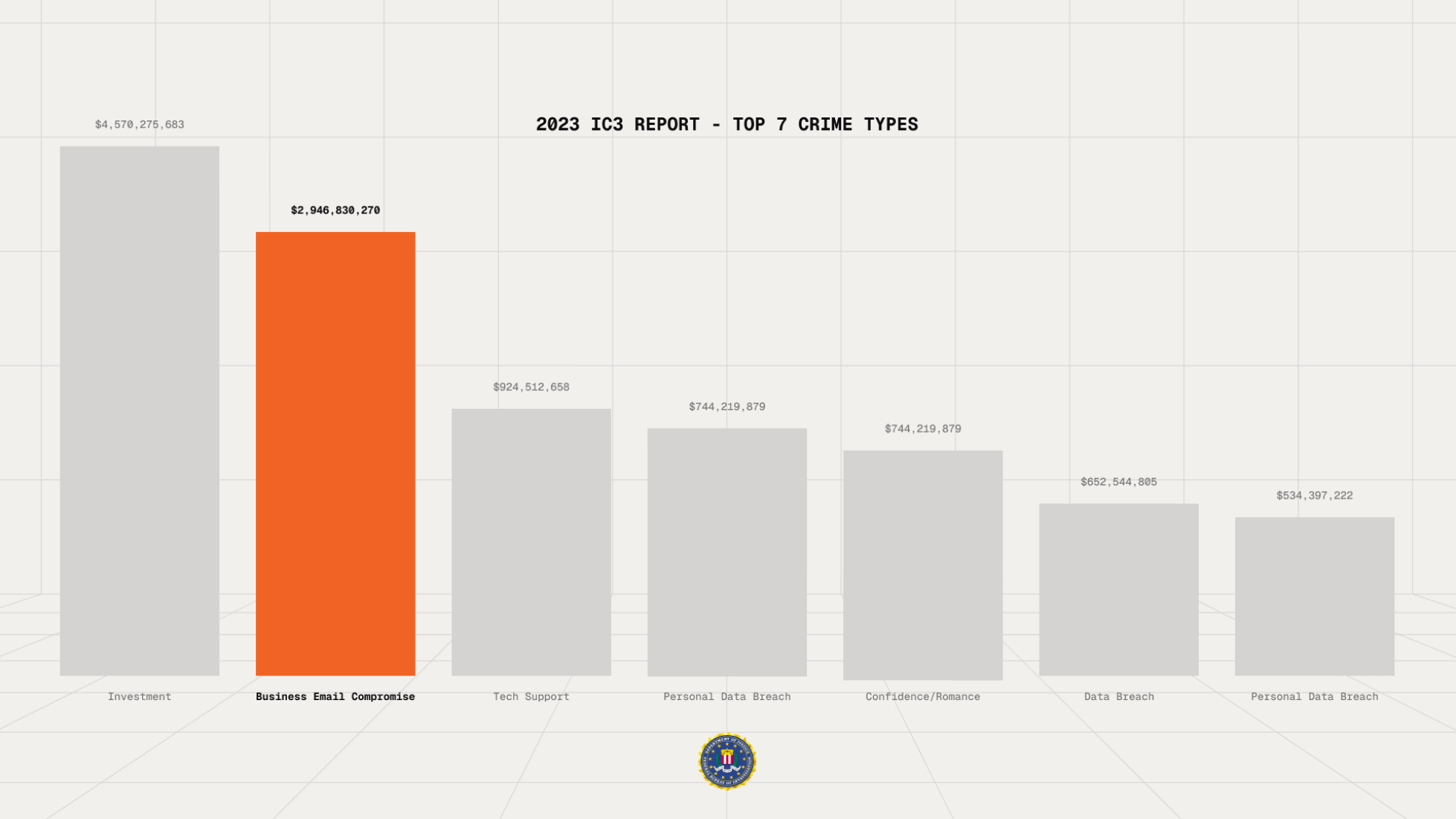
And this lack of built in email security costs enterprises billions. 90% of data breaches start with a phishing email. In 2023 alone, the FBI reported $2.9 billion in losses from business email compromise (BEC) scams.
With generative AI enabling near zero cost for highly personalized and effective phishing campaigns, traditional email security providers are stuck in an accelerated arms race to distinguish real emails from the fakes.
As we swiped Junk on more and more fake emails, we became frustrated with why emails themselves weren’t properly authenticated. With the latest advances in passkey technologies and new email protocol standards like RFC 5322, we knew this was now possible.
So we decided to build that deterministic authentication layer.
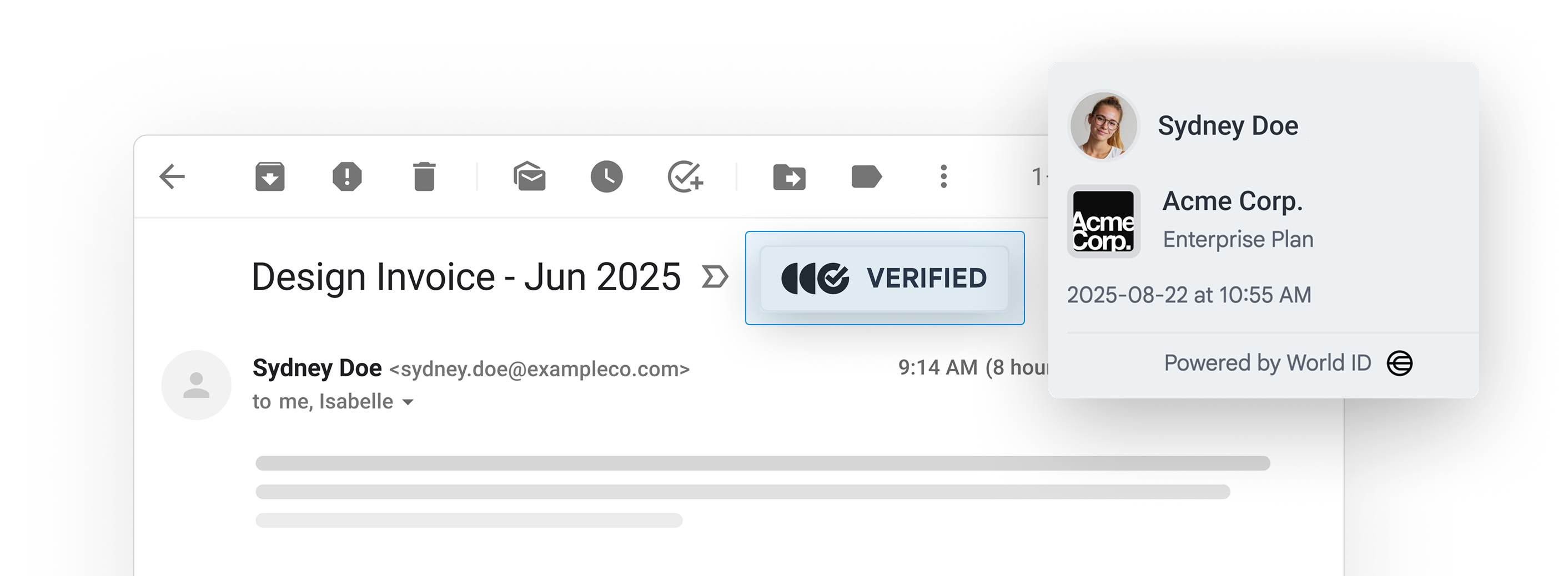
Outtake Verify isn’t like existing SEGs (Secure Email Gateways) that set rules and probabilistically filter out spam and phishing emails. Instead, Outtake Verify is a deterministic process that allows senders to verify their identity on-the-fly when they send sensitive emails - preventing both impersonation and account takeovers.
Verified emails will appear with a "Verified Badge" to recipients who also have the extension installed, illustrating who actually pressed the Send button with 100% certainty.
Verify can be layered in an enterprise’s existing email security stack to require Verification on workflows that meet certain sensitivity criteria or to enable focused inboxes for Verified messages, filtering out all unverified messages. The Verify web extension supports Gmail and Superhuman, with Outlook coming soon!)
Verify blends cutting-edge cryptography with effortless device-based verification, all without storing or transmitting your raw emails to Outtake’s servers. Here's the high-level breakdown:
Secure Onboarding: Tie Email and Identity to User Device
Participating organizations first onboard by verifying ownership of their domain, logo, and other relevant business assets.
When an employee accepts an invitation to join, their full name, role and organization are registered at verify.outtake.ai via enterprise SSO/HRIS systems.
Employees tie their identity information to a passkey only they can unlock on their device, via standard FIDO options or World ID. Identity information from SSO is not stored on this passkey.
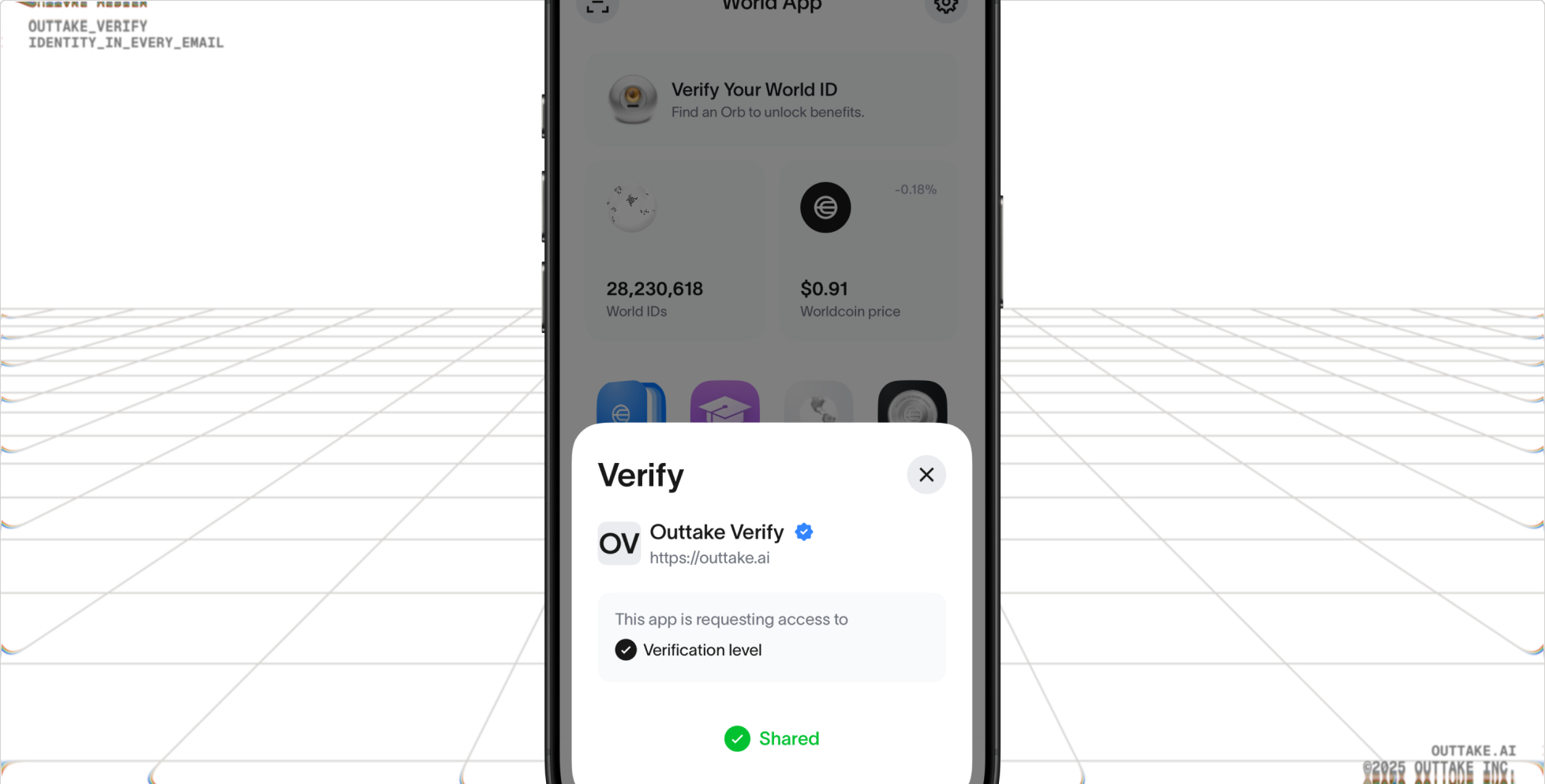
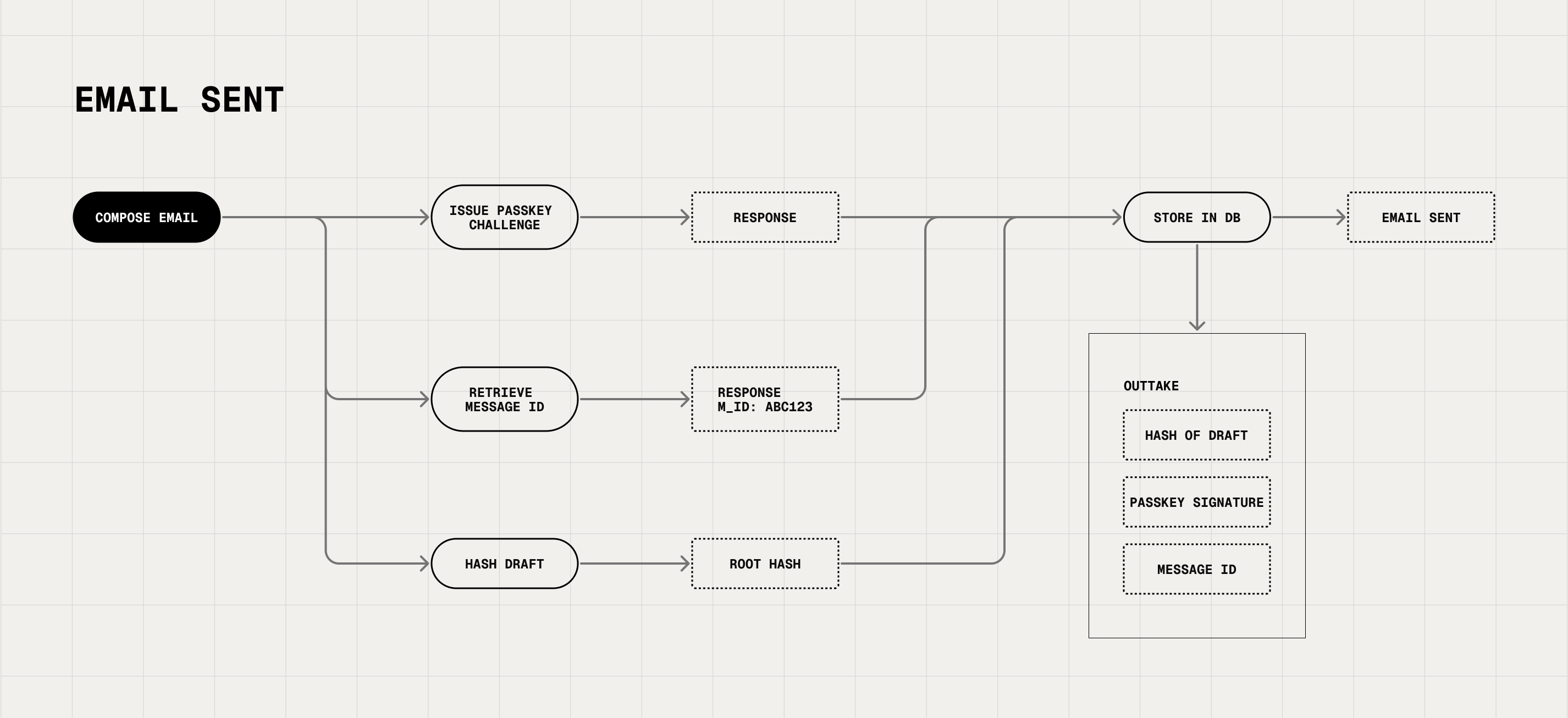
Sending Emails: Authenticate
Once finished composing an email, an employee hits the "Send" button, which is rendered by our extension as "Send Verified."
The employee is challenged to authenticate every few hours to every day, depending on your organization's security preferences.
Behind the scenes, the Verify for Email web extension hashes the email content and builds a Merkle Tree (the foundation of Git and Bitcoin) — a tamper-proof structure that securely hashes the message. No raw emails are sent to Outtake or stored. We save the hash. Everything else happens on the device.
Attackers can't fake this process; they'd need access to the passkey that employees unlock on their device via password or biometrics. Yet, to you and your employees, it's simple and easy - no IT overhauls required.
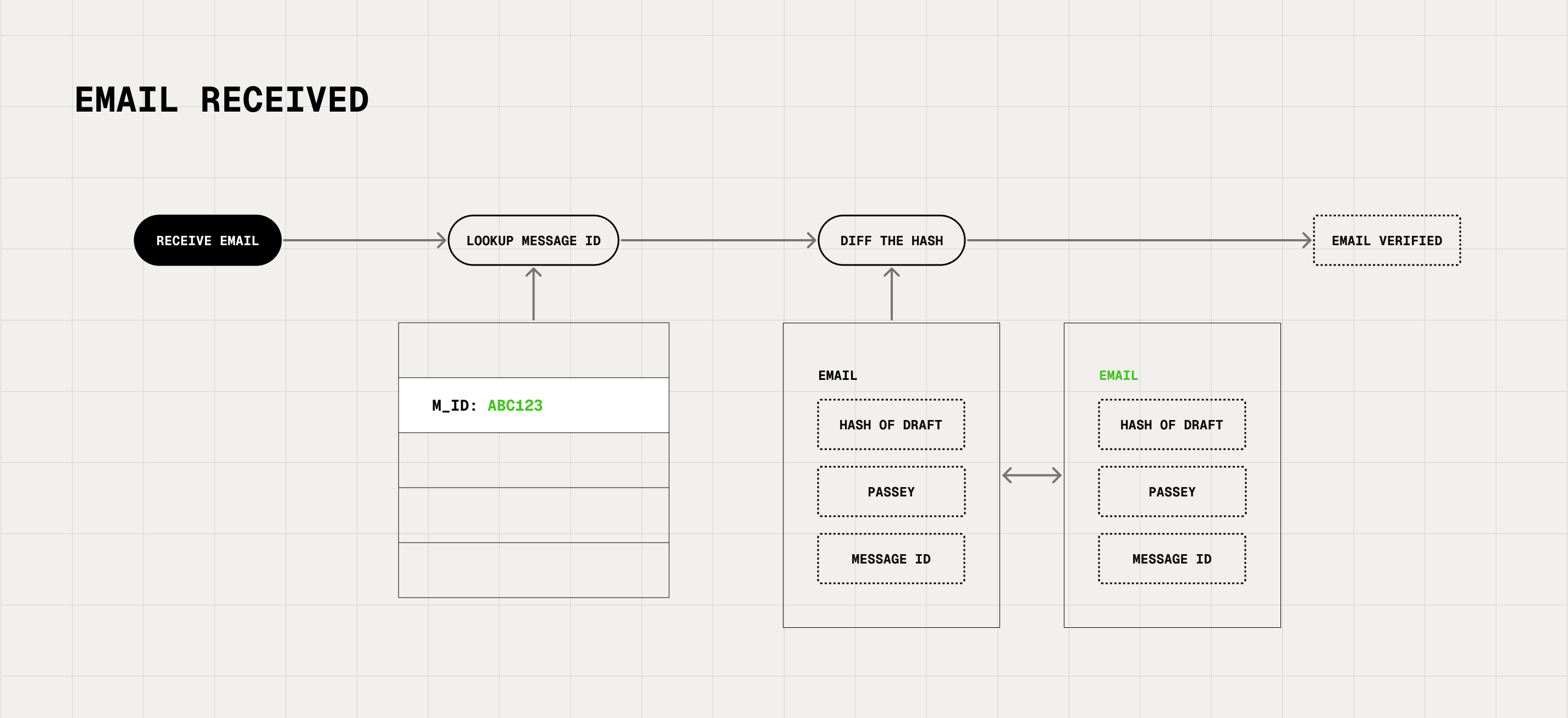
Receiving Emails: Instant Verification Badge
If the email recipient also has Verify installed, Verify will detect if the hash of the incoming email matches the hash of the sent email. If there is a match, a Verified badge immediately appears in the recipient’s email client, confirming the email was sent by the expected person and was not tampered in transit.
No more second-guessing or out of band confirmations required - you’re sending and receiving emails that you know you can trust.
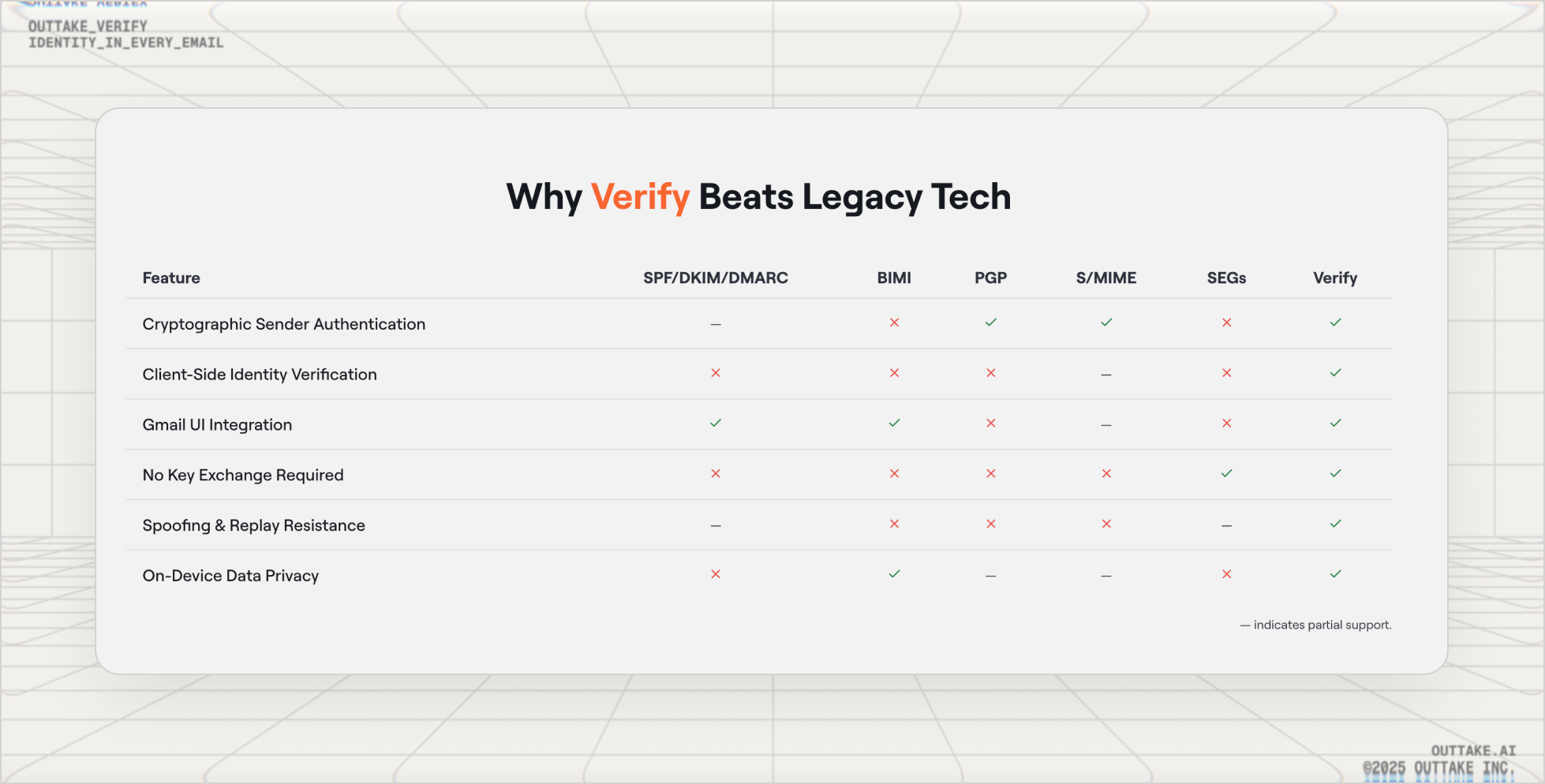
Email has a long history of email policies, with mixed outcomes. Unlike existing policies like SPF, DKIM, and DMARC, Verify adds a layer that is tied to your identity, so the recipient can trust that you work where you claim to work, and that you are who you claim to be.
Furthermore, unlike S/MIME or PGP/GPG, Verify does not rely on encryption, key-sharing, or Web of Trust techniques. Instead, Verify sends your emails as-is; verification occurs in the background via privacy-preserving lookups against a table of verified email hashes.
Finally, although modern email security products using ML to detect phishing are powerful, they still have false positives and false negatives. In contrast, Verify’s deterministic nature means messages are Verified or not. This also means Verify doesn't suffer from the expensive process of training a classifier against your organization's inbox, it doesn't require cumbersome setup in your email environment, and it will never delay messages from hitting your inbox on time.
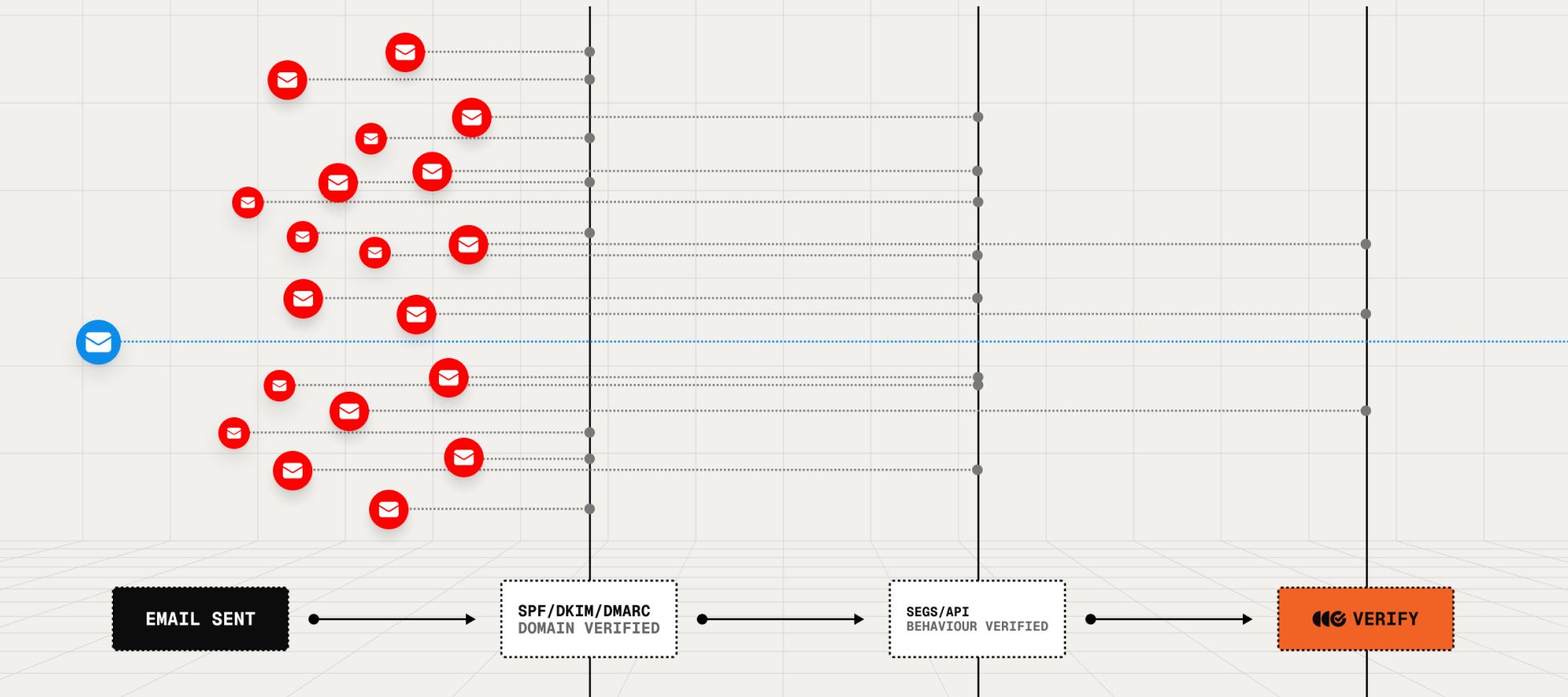
Phishing and account takeovers aren't slowing down- they are evolving faster with AI. Don't wait for the next breach.
Outtake Verify solves this: building identity into every email, deterministically.
Join leading cyber-conscious enterprises in securing emails. Request access to our closed beta to learn more today.
