Introduction
We're thrilled to announce Outtake Verify for Email!
Designed for enterprise teams using email for sensitive communications, Outtake Verify authenticates sender identity and conveys this assurance to recipients- allowing your business to move at the speed of trust even in the face of increasing digital threats. It's free to start, easy to deploy, and available now.
Ready to never second-guess an email again?
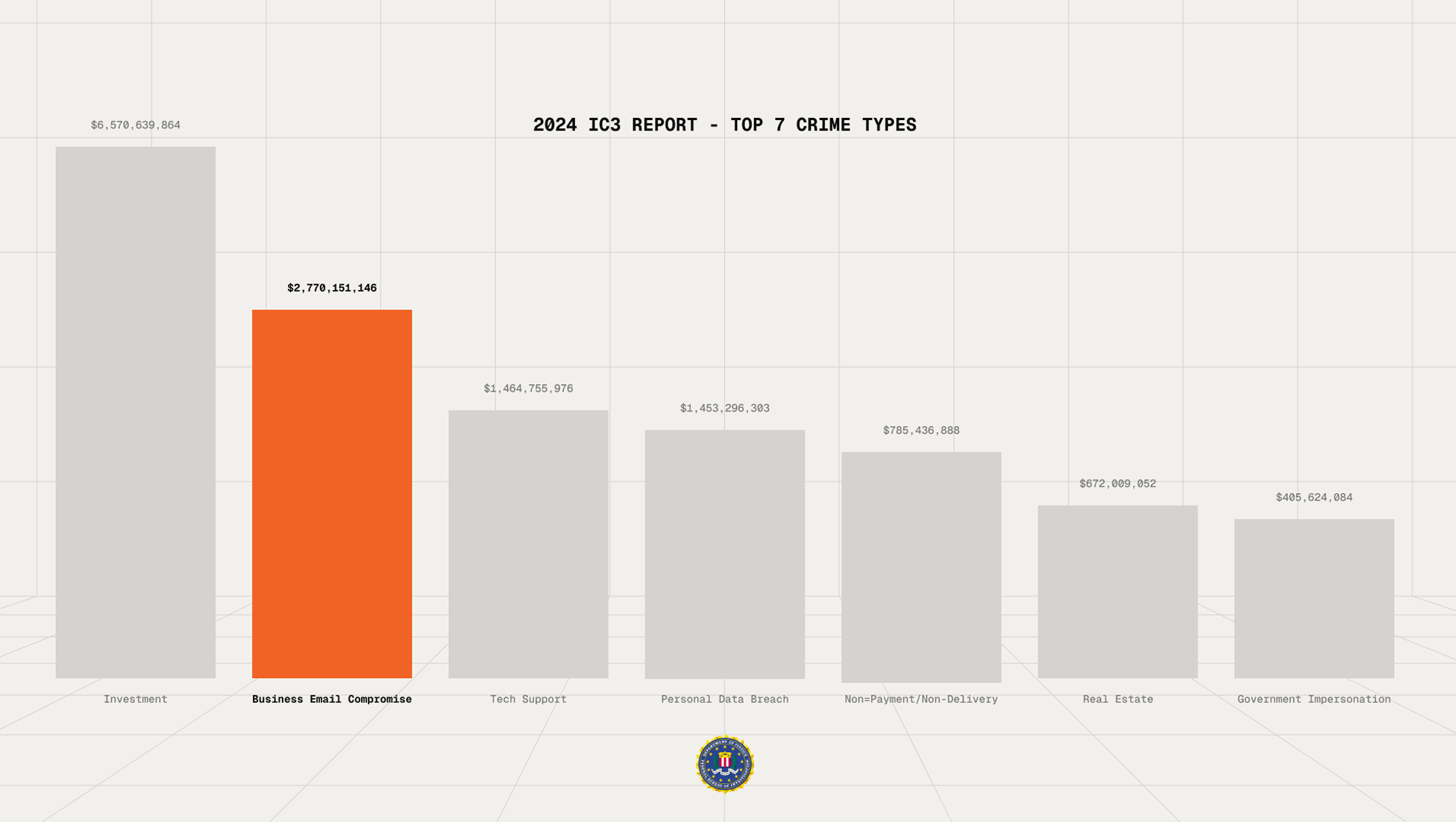
The $2.8 Billion Problem Hidden in Your Inbox
The FBI reported $2.8 billion in losses from business email compromise ("BEC") in 2024 alone. This phishing problem is foundational in email. Email was built in the 1970s for messaging, not security. Fast forward to today, and anyone can spoof a domain, set up the MX records and craft a convincing message that lures you into an account hijack. With generative AI dropping the cost of sophisticated phishing to near zero, traditional security vendors are fighting an accelerated arms race.
At Outtake we felt this firsthand. We get phishing emails that impersonate me as CEO, include fake invoices, eSignature links, or request urgent wire transfers. Our security stack catches most—but "most" isn't enough when one successful attempt could compromise everything.
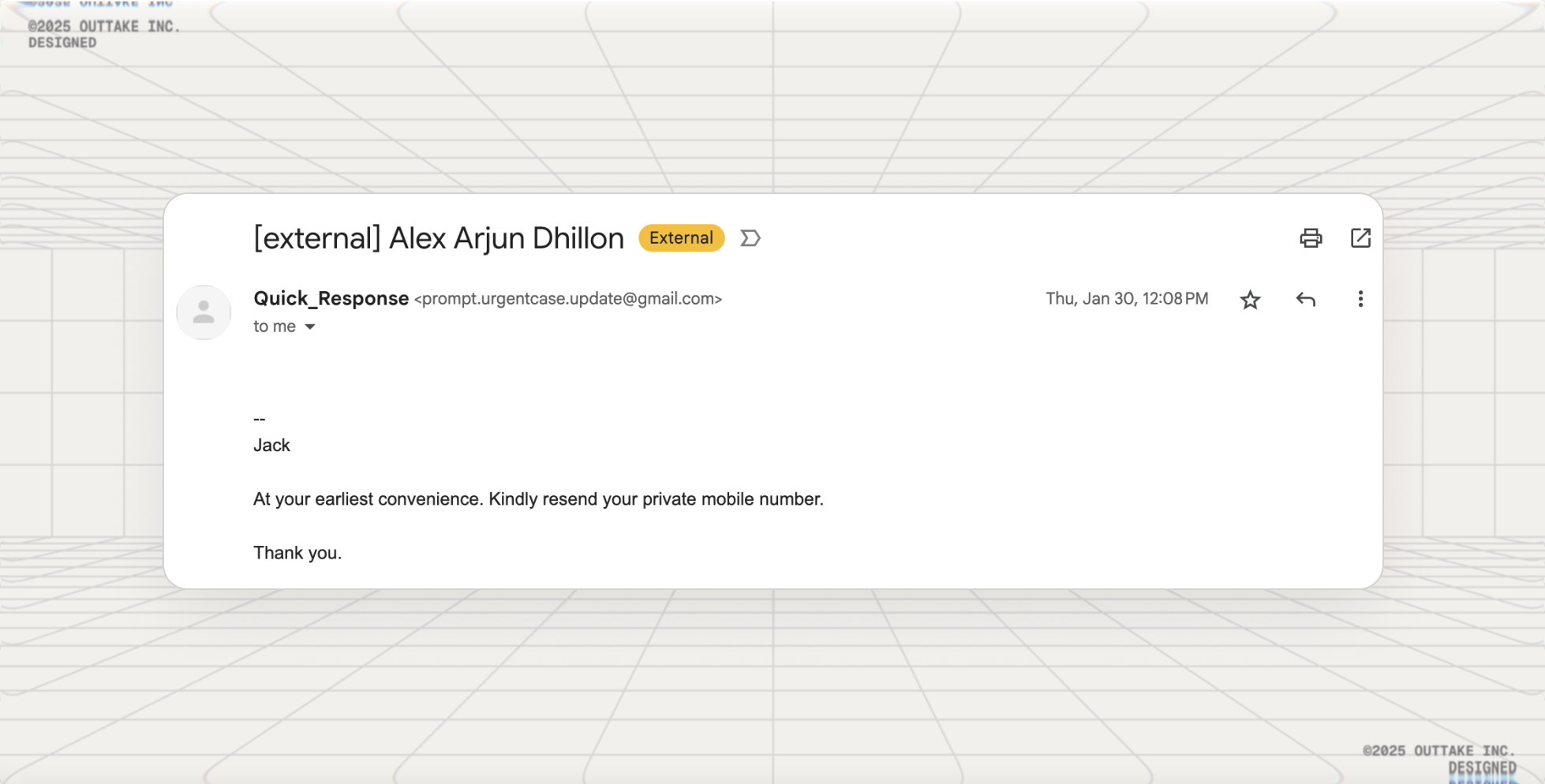
As we pressed “report” on a never-ending stream of fakes, we kept asking: why can't email just prove who actually pressed send? With advances in passkeys, email protocols and device-bound authentication, we realized it finally could.
Meet Outtake Verify: Identity Built Into Every Email
Outtake Verify for Email adds what email should have had from the beginning: deterministic sender authentication tied to identity and user device.
Outtake Verify allows you to be confident the email you are reading really came from who you think sent it.
Unlike probabilistic solutions that guess whether an email address is spam and never know if a real email has been compromised, Outtake Verify provides certainty.
When you see a Verified badge, you know who pressed send.
How It Works
Step 1: Secure Onboarding
When a company invites employees to use Outtake Verify, the system validates user identity through the company's Single-Sign-On (SSO) and HR Information Systems (HRIS), linking the user’s email address to name and position. Employees tie their identity information to an authentication method only they can access - such as passkey or World ID. No certificates to manage, no keys to distribute.

Step 2: Sending Verified Emails
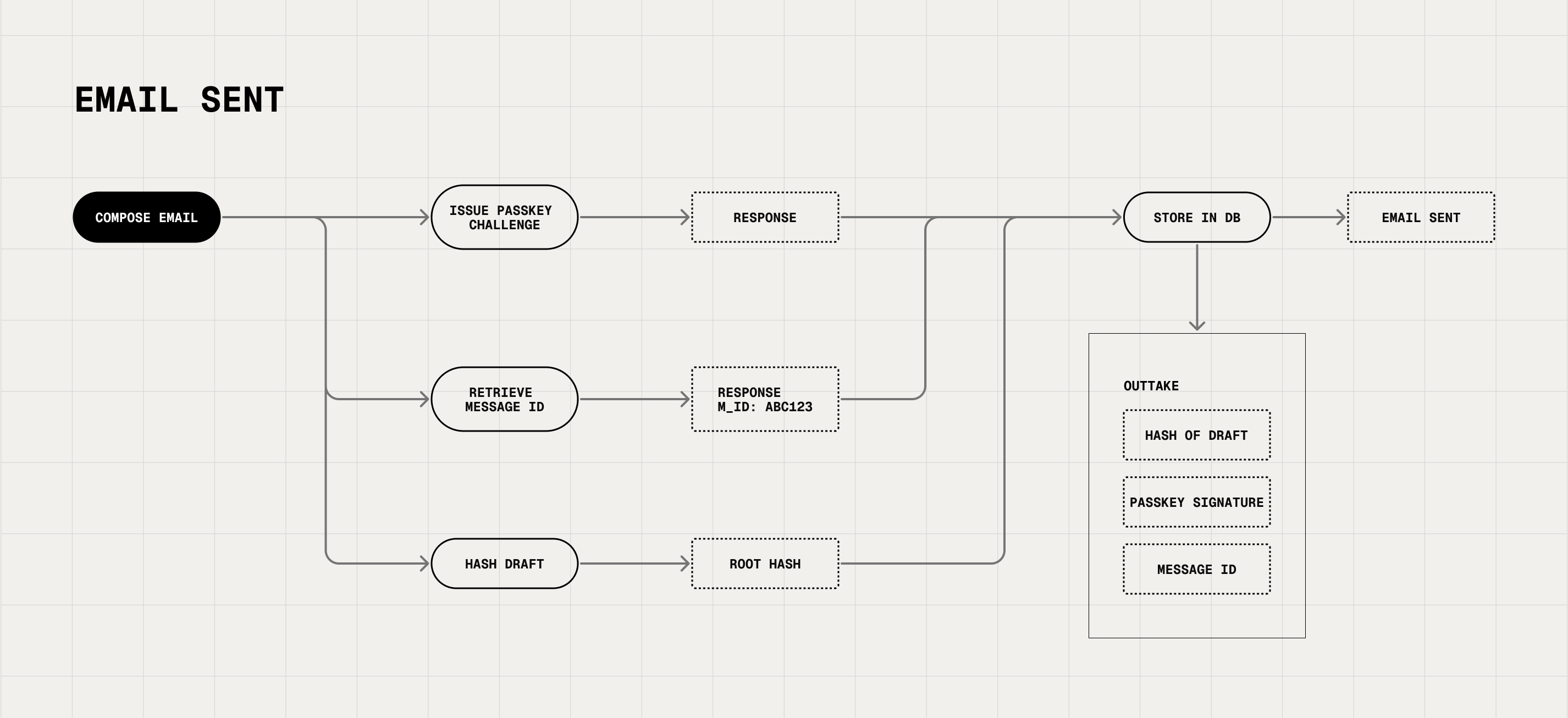
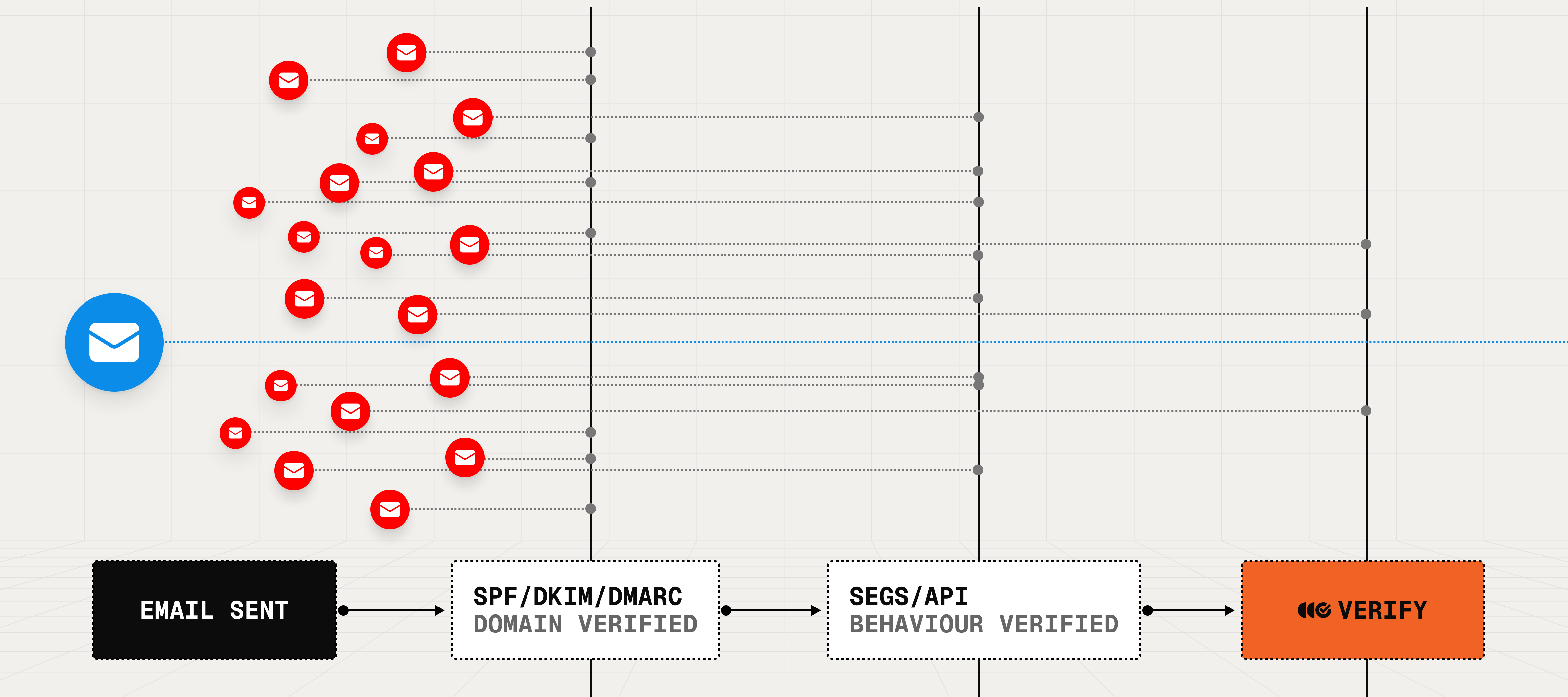
An enterprise can install the extension on employee browsers. Users compose emails normally, then hit “Send Verified" and authenticate using their chosen method. Note, each IT administrator can configure authentication session duration for optimal usability. Outtake Verify hashes email content locally and creates tamper-proof verification records using Merkle Trees (the foundation of Git and Bitcoin). Everything happens on-device—Outtake never sees your raw emails or addressees, only cryptographic hashes.
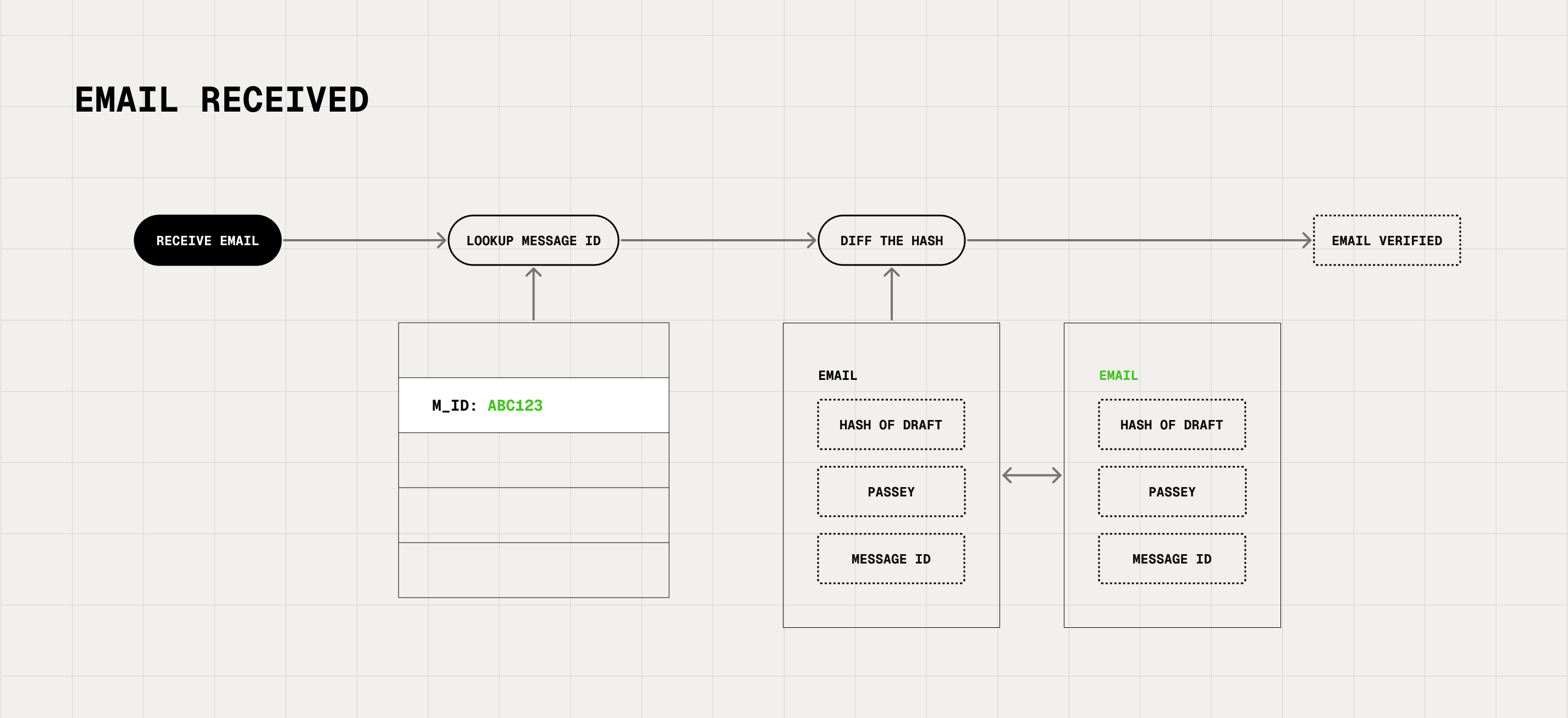
Step 3: Receiving Verified Emails
Recipients with Verify see a Verified badge confirming sender identity and message integrity. Users can hover for full sender details: photo, name, position, and company. Users can filter their inbox to show only Verified emails or request counterparts Verify as needed.
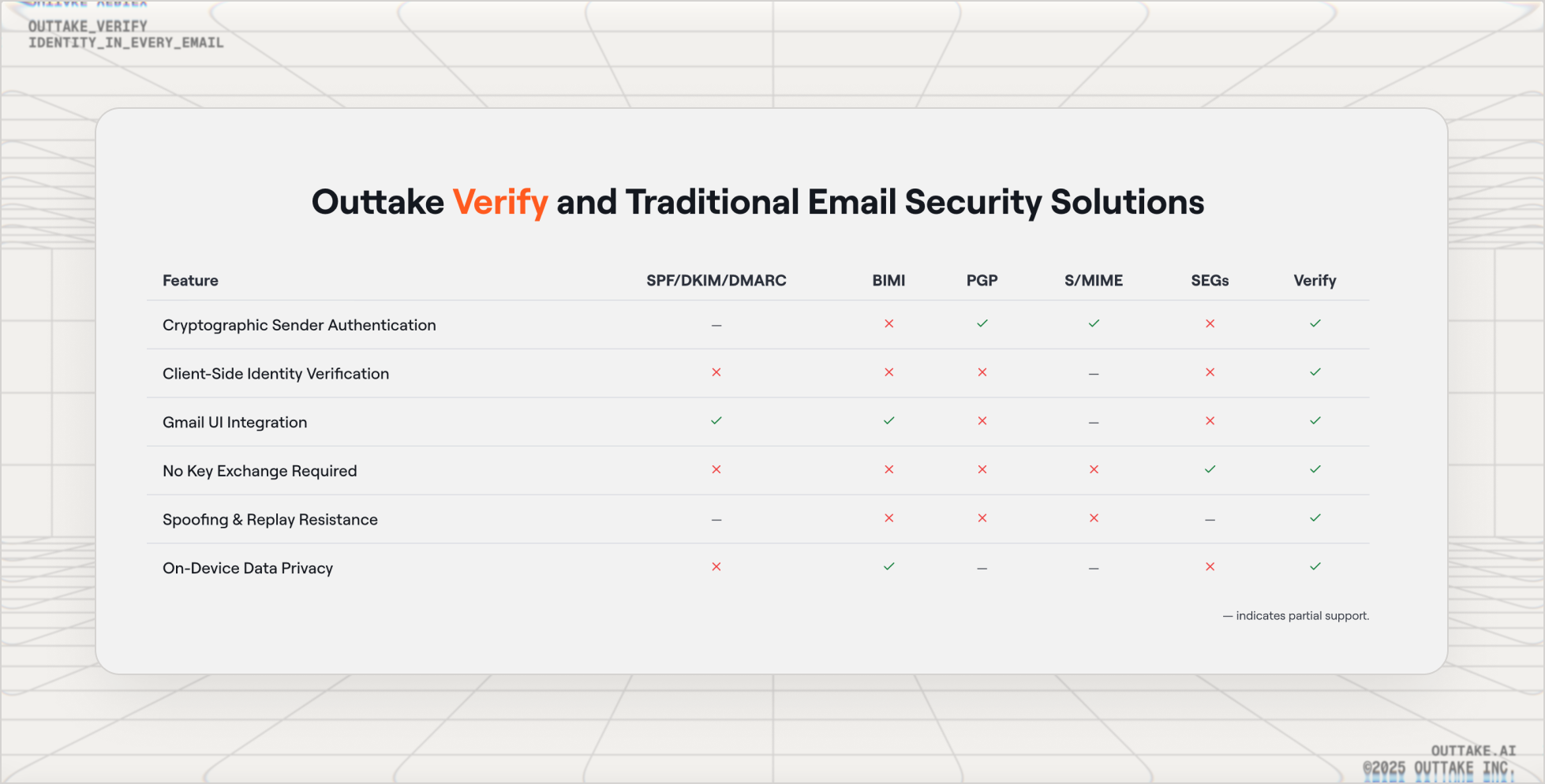
How Outtake Verify is Different from Traditional Email Security Solutions
- SPF/DKIM/DMARC authenticate domains, not people. Compromised accounts sail right through.
- S/MIME and PGP require complex key exchange
- Secure Email Gateway and ML-based filters generate false positives on legitimate emails and miss sophisticated attacks.
Outtake Verify operates alongside these solutions, adding the missing piece: identity verification tied to real people on real devices.
Why Enterprises Need Verify: Real World Impact
- Sensitive requests from executives or vendors are cryptographically verifiable, reducing the need for out-of-band confirmations and accelerating business velocity.
- Account takeover attacks cannot send Verified because they lack device-bound authentication.
- Sensitive document exchanges happen with certainty about sender identity, streamlining compliance workflows.
- Network-wide trust extends to partners and vendors in the Outtake Verify ecosystem.
Deploy Outtake Verify in your Organization in Minutes
Unlike traditional email security overhauls, Outtake Verify deploys via:
- One-click installation through Chrome extension management
- Integration with existing SSO (no new identity provider required)
- Works within Gmail and Superhuman today; Outlook coming soon
- No MX record changes or email routing modifications
- No user training beyond "authenticate when prompted"
Get Started Today
Email's authentication gap has persisted for 50 years. With AI-powered attacks evolving faster than defenses, that gap is growing. Outtake Verify closes it—deterministically, privately, and without disrupting your operations.
Free for early enterprise adopters. Because the best time to add authentication to email was 1971. The second best time is now.
Schedule a demo • Read our technical FAQ
Outtake Verify is available now for Gmail and Superhuman, with Outlook support coming soon.







